The Cyber Security and Resilience Bill: What Finance Directors Need to Do Before It Becomes UK Law

204 nationally significant cyber attacks hit the UK in the year to August 2025. That is a 130% increase on the previous year. Tough new laws are now on their way that will change what the state expects of your suppliers and, indirectly, of your board.
Here is the scene: Your IT manager mentions something about new cyber regulations. Your MSP sends a vague email about “upcoming compliance changes.” You file both under “will deal with later.”
Later is now.
The Cyber Security and Resilience Bill was introduced to Parliament in November 2025 and is now progressing through its stages. When it passes in 2026, it will be the biggest overhaul of UK cyber law in a decade.
If you are a Finance Director with IT in your remit, three things in this Bill should concern you now. Not because you run a power station. But because the rules are about to reach your suppliers, your IT providers, and the governance standards your board will be judged against.
What the Bill Actually Does
The Bill updates and replaces the UK’s existing Network and Information Systems (NIS) regime. In plain language, it does four things.
It expands who is regulated. Medium and large Managed Service Providers - the outsourced IT companies that run your servers, manage your helpdesk, handle your backups - are now in scope. So are data centres, cloud providers and other critical suppliers that support essential services. If your MSP has access to your systems, they will have legal duties they did not have before.
It tightens incident reporting. If an in‑scope organisation suffers a significant cyber incident, it will have to notify its regulator and the National Cyber Security Centre within 24 hours, with a fuller report within 72 hours. Today, many incidents only get reported when they actually disrupt a service. Under the new regime, incidents that could cause serious disruption or damage, including serious “near misses”, will have to be reported too.
It creates supply‑chain accountability. Regulators will be able to designate “critical suppliers” to essential services — such as data centres, diagnostics providers, or IT support firms — and impose security and reporting duties on them. In practice, this means more scrutiny of how risk is managed through your outsourced IT and cloud contracts.
It strengthens enforcement and penalties. Regulators will gain modernised powers to inspect, investigate and enforce cyber resilience standards, backed by tougher, turnover‑based penalties for serious failures, including the ability to levy substantial multi‑million‑pound fines and daily penalties for ongoing non‑compliance. The intent is clear: it must no longer be cheaper to cut corners than to invest in resilience.
Why This Matters If You Are Not a Regulated Entity
You may be thinking: “We are not the NHS. We are not a rail operator. This does not apply to us.”
You are probably not directly in scope. But it affects your world in three ways that hit your risk register and your P&L.
Your MSP is now regulated. The IT company that manages your infrastructure, your email and your cloud will have legal duties around security and incident reporting if they are medium or large in size. They will have to meet minimum standards and report serious incidents quickly. If they cannot comply, you have a supplier risk. If they have a breach and you never asked basic questions, you have a governance problem.
Your contracts are probably not fit for purpose. Most mid‑market MSP contracts were written before this Bill existed. They will not mention 24‑hour incident notification. They will not reflect the new reporting duties. They may not give you visibility of your MSP’s own supply chain. When the Bill passes, your provider will have obligations to their regulator. Whether they have clear obligations to you depends entirely on what your contract says.
Board scrutiny is increasing. Government and the NCSC have been unambiguous: cyber resilience is a board‑level governance issue, not an IT issue. At the same time, only around a quarter of UK businesses say a board member is formally responsible for cyber security. If IT reports to you, that expectation lands on your desk.
The Personal Accountability Question
This is the part most FDs have not heard about, and it is where you need a clear head.
The UK’s Cyber Security and Resilience Bill, as described in the government announcement, does not itself create explicit personal legal liability for directors if cyber controls fail. It focuses on organisations, regulators and supply chains.
However, two other pieces move the dial for you:
- The UK Corporate Governance Code 2024 (Provision 29) expects boards of premium‑listed companies to monitor, review and report on the effectiveness of all material controls — financial, operational and compliance — from 2026.
- The EU’s NIS2 Directive (which the UK is not implementing, but is widely referenced in commentary) explicitly requires directors in in‑scope organisations to approve cyber risk measures, oversee implementation and receive training, with powers for regulators to sanction individuals.
Put simply: even though this Bill does not write personal cyber liability for directors into law, the direction of travel is towards visible, documented board‑level oversight of cyber risk. If there is a serious incident, a regulator, auditor, insurer or buyer will ask: “What did the board do to manage this risk?” If the honest answer is “we left it to IT,” that will not look like reasonable oversight.
You do not need to become a security expert. But you do need to be able to show that your board asked the right questions and took proportionate action.
Five Things to Do
You do not need to read a Bill or memorise acronyms. You need to do five specific things that fit squarely in your skill set as a Finance Director.
1. Ask Your MSP Three Questions
Send an email to the person who manages your IT outsourcing relationship. Ask:
- Are you aware of the Cyber Security and Resilience Bill, and what is your plan to comply with the new regime? If they say “what Bill?” — that is your first red flag.
- If you suffer a cyber incident that affects our data or systems, how will you notify us and within what timeframe? The Bill will push them to notify regulators quickly. Your contract should require them to notify you at least as fast.
- Can you provide evidence of your current security posture? Cyber Essentials certification is the minimum. Cyber Essentials Plus or ISO 27001 is better. If they have neither, ask why.
You are not trying to audit them. You are trying to find out whether they take this seriously and have a plan.
2. Review Your MSP Contract
Pull out the contract. Look for five things:
Incident notification clause. Does it require your MSP to notify you of a security incident? Within what timeframe? If it says “within 30 days” or is silent, that is not aligned with the 24/72‑hour reporting world they are moving into.
Data portability. If you needed to leave, can you get your data out quickly and in a usable format? At what cost? A provider that makes exit hard is a provider that increases your risk.
Right to audit. Can you (or a third party you appoint) review their security controls, or at least their certifications and key policies? If not, you are trusting without verifying.
Liability cap. If their failure leads to a breach or outage that costs you money, what is their liability? Many MSPs cap it at 12 months’ fees. If they manage systems that underpin millions of pounds of revenue, that cap may be out of line with your risk.
Sub‑contracting. Do they use other providers behind the scenes (for example, another company for out‑of‑hours support or overseas for network monitoring)? If so, is that transparent in the contract, and do your protections flow down?
If your contract is missing two or more of these, it needs a refresh before the Bill takes effect in 2026, not after.
3. Put Cyber on the Board Agenda
You do not need a glossy deck. You need a standing item once a quarter that answers four questions:
- What are our critical digital assets? The systems and data that, if compromised, would stop us trading or get us into regulatory trouble.
- What happened since the last meeting? Any incidents, near misses, supplier issues or major changes to the threat landscape. (This could be a monthly agenda item.)
- What is the status of our key controls? Patching, backups, access management, staff awareness training, and are they in place and working?
- What decisions are needed? Budget approvals, policy changes, supplier actions, or changes in risk appetite.
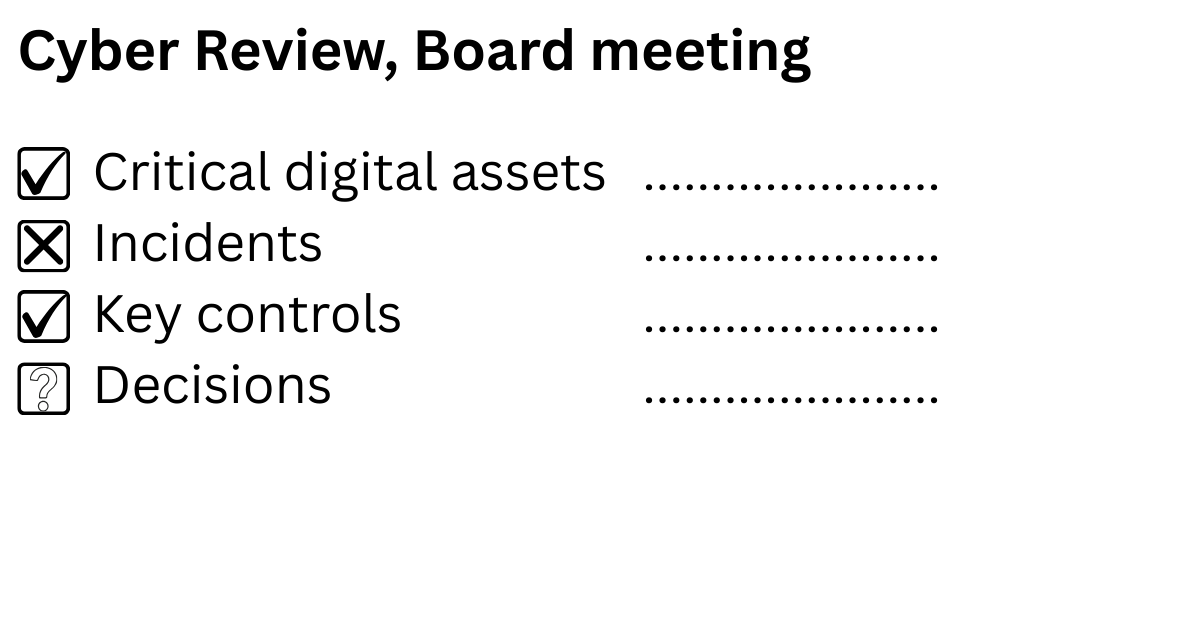
One page. Four questions. Fifteen minutes. That is what proportionate board‑level cyber governance looks like in a mid‑market business, and it is the evidence trail you may need.
4. Check Your Cyber Insurance
Pull out your cyber insurance policy and read it the way you would read a leveraged finance covenant.
Ask:
- Does it cover regulatory investigations and associated costs? Some policies only cover certain types of regulatory action, and most won't cover fines.
- Does it cover incidents caused by your MSP or other suppliers? If your MSP is breached and you are taken offline, are you covered?
- What security conditions does it impose? Many policies assume you have basic controls like multi‑factor authentication, offline backups and a tested incident response plan. If you do not, the insurer may decline a claim.
- What is the notification window? If you are required to notify the insurer within 24 or 48 hours of discovering an incident, but your MSP takes a week to tell you, you have a problem.
Cyber insurance is not a substitute for controls. But if you are paying for it, make sure it would actually respond in the scenario you care about.
5. Run a Simple Cyber Risk Assessment
You do not need a 60‑page report. You need a one‑page table. Sit down with your IT manager or MSP and fill in something like this:
| Asset | What happens if it is compromised | How likely (H/M/L) | What controls are in place | What is missing |
|---|---|---|---|---|
| Email system | Phishing, fraud, business disruption | High | MFA, spam filtering | No staff training in last 12 months |
| Finance / ERP | Fraud, data loss, regulatory breach | Medium | Role‑based access, daily backups | No recent restore test |
| Customer database | GDPR breach, reputational damage | Medium | Encryption at rest, limited access | No access review for 24 months |
| Website / e‑commerce | Revenue loss, brand damage | Low | WAF, SSL, monitoring | No documented incident response runbook |
| Backup systems | Cannot recover from ransomware or data corruption | High | Daily backup to separate environment | No periodic offline backup, no test |
The output is not a certificate. It is a prioritised list of actions. For example: “We need to test our backups quarterly” or “We need MFA turned on everywhere this quarter, not next year.”
What This Costs, and What It Saves
None of the steps above require major spend.
- The MSP questions cost nothing.
- The contract review is a conversation with your legal adviser or a half‑day of external support.
- The board agenda item is fifteen minutes per quarter.
- The insurance review is an afternoon.
- The risk assessment is a two‑hour working session.
The cost of not doing them is harder to forecast but easy to imagine.
Government’s Cyber Security Breaches Survey 2025 reports that 43% of UK businesses identified a cyber breach or attack in the previous 12 months; for medium‑sized businesses, that figure is closer to two‑thirds. The average cost of the most disruptive breach for a business that experiences one runs into tens or hundreds of thousands once you factor in staff time, recovery work, lost output and reputational damage.
When a breach hits, the first questions from your board, your insurer and any regulator will be: Did we know this risk existed? What did we do about it? Who owned it?
Your answers to those questions are worth more than any single security product.
The Timeline
The Bill is going through Parliament now, with Royal Assent expected in 2026 and detailed implementation to follow via secondary regulations. Some obligations will bite quickly. Others may come with a transition period.
You have a window. Use it.
The five steps above take less than 90 days. They cost very little. They give you a defensible position when the Bill becomes law and a much clearer view of where your real cyber risks sit.
If you wait until the Bill passes, you will be competing with every other mid‑market business for the same legal advice, the same contract renegotiations and the same MSP attention. The FDs who move now will get better terms, better answers and better protection.
If You Want Help
I work with Finance Directors and boards who carry IT in their remit but do not have a CTO or CIO on the Executive Board.
If you want a 30‑minute conversation about how this Bill affects your business specifically, and what your first move should be, book a call. No charge. No follow‑up unless you ask for one.
Or send me your most pressing question: hello@mikefraser.me. I will answer it within 48 hours.
